Is Australia a sitting duck for ransomware attacks? Yes, and the danger has been growing for 30 years
- Written by Paul Haskell-Dowland, Associate Dean (Computing and Security), Edith Cowan University
Australian organisations are a soft target for ransomware attacks, say experts who yesterday issued a fresh warning[1] that the government needs to do more to stop agencies and businesses falling prey to cyber-crime. But in truth, the danger has been growing worldwide for more than three decades.
Despite being a relatively new concept to the public, ransomware has roots in the late 1980s and has evolved significantly over the past decade, reaping billions of dollars in ill-gotten gains.
With names like Bad Rabbit, Chimera and GoldenEye, ransomware has established a mythical quality with an allure of mystery and fascination. Unless, of course, you are the target.
Victims have few options available to them; refusing to pay the ransom depends on having good enough backup practices to recover the corrupted or stolen data.
According to a study by security company Coveware[2], 51% of businesses surveyed were hit with some type of ransomware in 2020. More concerningly still, typical ransom demands are climbing dramatically, from an average of US$6,000 in 2018, to US$84,000 in 2019, and a staggering US$178,000 in 2020.
A brief history of ransomware
The first known example of ransomware dates back to 1988-89. Joseph Popp, a biologist, distributed floppy disks containing a survey (the “AIDS Information Introductory Diskette”) to determine AIDS infection risks. Some 20,000 of them were reportedly distributed at a World Health Organization conference and via postal mailing lists. Unbeknown to those receiving the disks, it contained a virus of its own. The AIDS Trojan[3] lay dormant on systems before locking users’ files and demanding a “licence fee” to restore access.
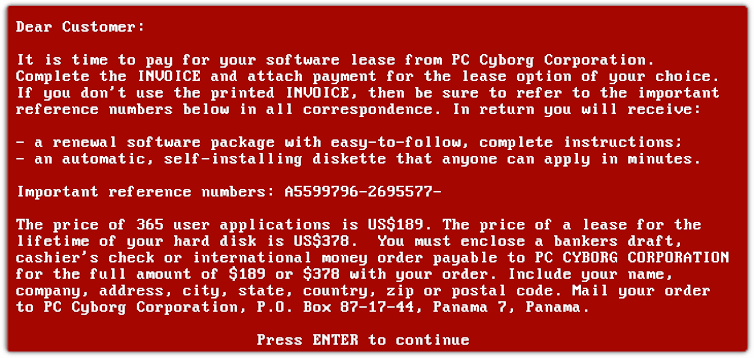 The 1989 AIDS Trojan (PC Cyborg) ransom demand.
Joseph L. Popp, AIDS Information Trojan author, Public domain, via Wikimedia Commons
The 1989 AIDS Trojan (PC Cyborg) ransom demand.
Joseph L. Popp, AIDS Information Trojan author, Public domain, via Wikimedia Commons
Although the malware was inelegant and easily undone[4], it drew media attention at the time as a new type of cyber threat. The demand for payment (by cheque to a PO box in Panama) was primitive by comparison with modern approaches, which call for funds to be transferred electronically, often in cryptocurrencies.
It was well over a decade before ransomware truly began to proliferate. In the mid-2000s, stronger encryption allowed for more effective ransom campaigns with the use of asymmetric cryptography (in which two keys are used: one to encrypt, and a second, kept secret by the criminals, to decrypt), which meant even skilled systems administrators could no longer extract the keys from the malware.
In 2013, CryptoLocker malware rose to global dominance, partly supported by the GameOver Zeus botnet[5]. Cryptolocker encrypted users’ files, sending the unlock key to a server controlled by the criminals with a three-day deadline before the key was destroyed. The network was shut down in 2014, thanks to a major global law enforcement effort called Operation Tovar[6]. It is estimated to have impacted more than 250,000 victims and potentially garnered 42,000 Bitcoin[7], worth around US$2 billion at today’s valuation.
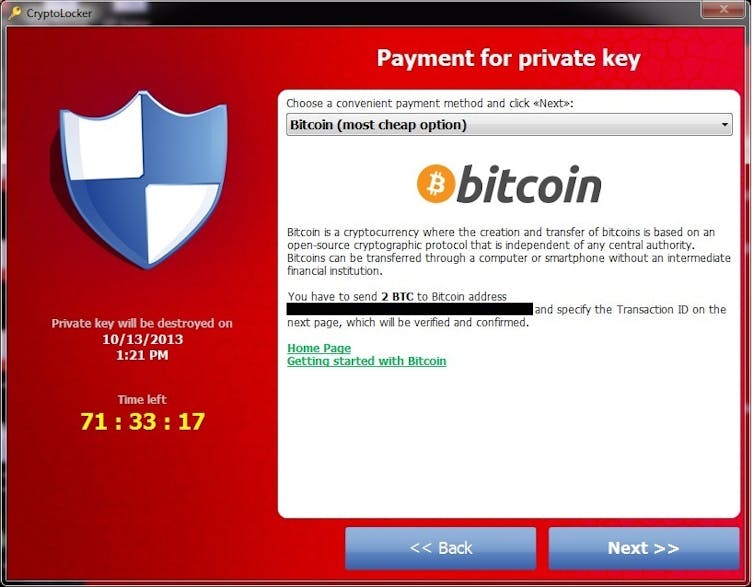 CryptoLocker ransom demand.
Nikolai Grigorik, CC BY-SA 4.0 https://creativecommons.org/licenses/by-sa/4.0, via Wikimedia Commons
CryptoLocker ransom demand.
Nikolai Grigorik, CC BY-SA 4.0 https://creativecommons.org/licenses/by-sa/4.0, via Wikimedia Commons
In 2016 there were several high-profile incidents involving the Petya ransomware, which prevented users from accessing their hard drives. It was one of the first significant examples of Ransomware as a Service[8], whereby criminal gangs “sell” their ransomware tools as a managed service.
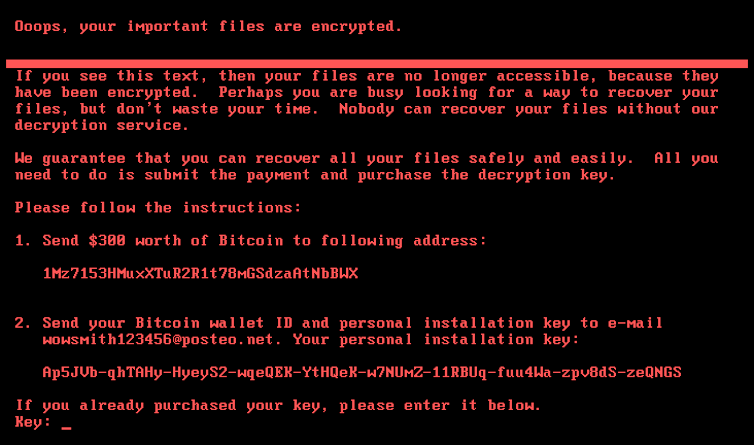 Petya ransom demand.
Unknown criminal. Notify the authorities, in case of discovery. Public domain, via Wikimedia Commons
Petya ransom demand.
Unknown criminal. Notify the authorities, in case of discovery. Public domain, via Wikimedia Commons
The following year saw arguably the most notorious ransomware attack of all time: the WannaCry attack. It struck hundreds of thousands of computers, including an estimated 70,000 systems at the UK National Health Service[9]. The global impact of WannaCry has been estimated at up to US$4 billion[10].
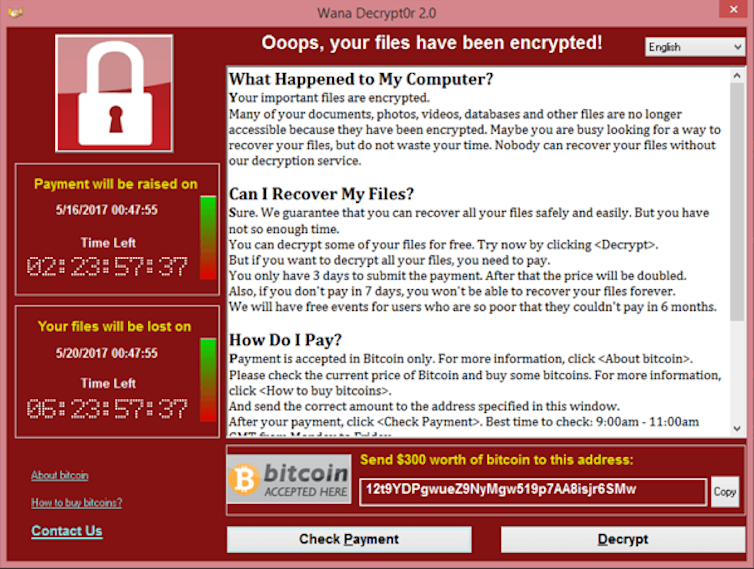 Wannacry ransom demand with integrated multi-language support.
Screenshot of a WannaCry ransomware attack on Windows 8. Public domain, via Wikimedia Commons
Wannacry ransom demand with integrated multi-language support.
Screenshot of a WannaCry ransomware attack on Windows 8. Public domain, via Wikimedia Commons
More recent still was the Ryuk[11] ransomware, which targeted local councils and national government agencies. But cyber-criminals have also attacked specific private companies, including the United States’ largest refined oil distribution network, Colonial Pipeline[12], the multinational meat processor JBS Foods[13], and Australia’s Channel Nine network[14].
Is all ransomware the same?
There are hundreds of types of ransomware, but they fit into a few broad categories:
Crypto ransomware
In modern crypto ransomware attacks, the malware encrypts users’ files (“locking” the files to make them unreadable) and will typically involve a “key” to unlock the files being stored on a remote server controlled by the cyber-criminals. Early variants would require the victim to buy software to unlock the files.
Locker ransomware
Locker ransomware is usually a more complex type of malware that targets a user’s entire operating system (such as Windows, macOS or Android), hampering their ability to use their device. Examples can include preventing the computer from booting, or forcing a ransom demand window to appear in the foreground and preventing interaction with the other applications.
Although files are not encrypted, the system is typically unusable by most users (as you would likely need another system or software to extract the files). In some cases the ransom demands refer to government agencies with threats of investigations relating to tax fraud, possession of child abuse materials, or terrorist activities.
 A fake FBI ‘seize’ notice designed to convince victims to pay the ‘fine’.
Motormille2, CC BY-SA 4.0 https://creativecommons.org/licenses/by-sa/4.0, via Wikimedia Commons
A fake FBI ‘seize’ notice designed to convince victims to pay the ‘fine’.
Motormille2, CC BY-SA 4.0 https://creativecommons.org/licenses/by-sa/4.0, via Wikimedia Commons
Leakware
In a leakware attack, the data are not encrypted but instead are stolen from the victim and held by cyber-criminals. It is the threat of public release alone that is used to secure a ransom payment. From 2020 to 2021, reported occurrences of non-encrypted ransoms have doubled[15].
Double extortion
Double extortion is an alarming development whereby not only is a payment required to secure release of encrypted organisation data, but there is the added threat of public release.
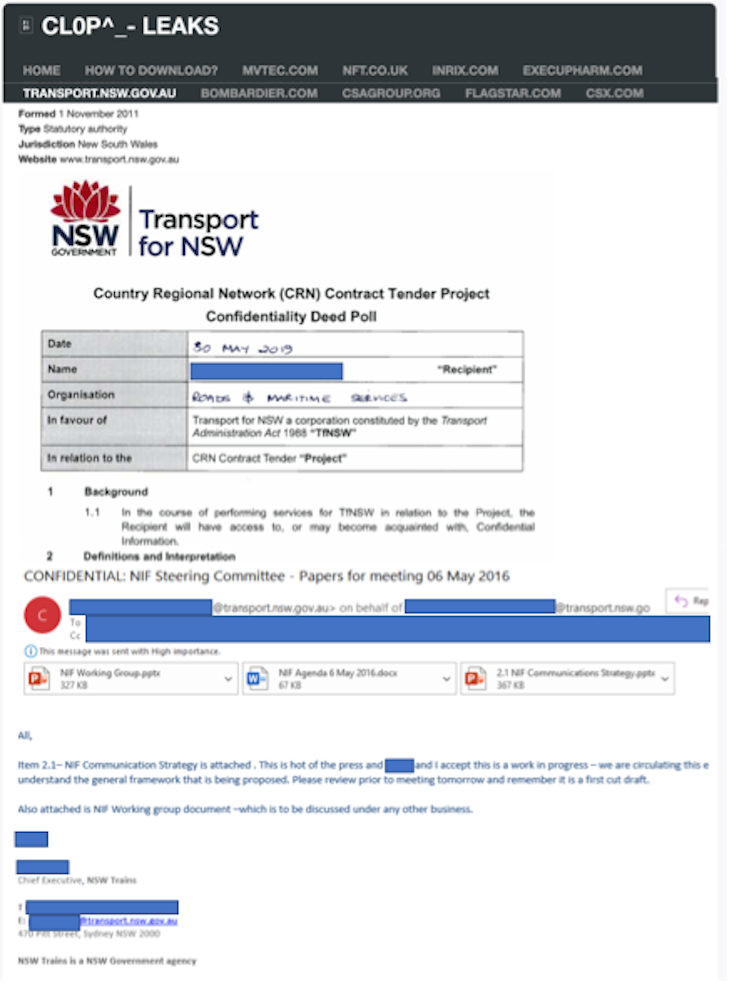 Screenshots from Cl0p leaks website providing access to stolen Transport NSW files (web version is not redacted).
Author provided
Screenshots from Cl0p leaks website providing access to stolen Transport NSW files (web version is not redacted).
Author provided
This approach typically involves data being stolen from the organisation during the malware infection process, then sent to servers run by the cyber-criminals. To encourage payment, extracts may be posted on public-facing websites to prove possession of the data – coupled with threats to publish the remaining data.
Ransomware as a Service (RaaS)
Early ransomware was developed by individuals but, as with all software, ransomware has come of age. It is now a multibillion-dollar industry (an estimated US$20 billion in 2020[16]) and is every bit as well designed and implemented as any commercial software.
Ransomware as a Service is here - and cheaper than you may think!Just as Microsoft’s Office 365 has developed into a service, where instead of buying the software, you pay a monthly or yearly subscription, so has ransomware. Ransomware as a Service[17] (RaaS) allows criminals to obtain services, typically in return for a cut of the ransom[18].
Read more: Holding the news to ransom? What we know so far about the Channel 9 cyber attack[19]
To pay, or not to pay?
Most law enforcement agencies recommend against ransom payments (just as many governments will not negotiate with terrorists), because it is likely to encourage future attacks. But many organisations nevertheless do pay up. Interestingly, the public sector hands over up to ten times more money[20] to release their files than victims in the private sector.
Paying a ransom is frequently seen as the lesser of two evils, particularly for smaller organisations that would otherwise be shut down entirely by the disruption to their systems. Or, if you are lucky, the malware will already have a publicly available antidote.
But paying the ransom doesn’t guarantee you’ll get all your data back. By one estimate[21], an average of 65% of data was typically recovered after paying the ransom, and only 8% of organisations managed to restore all of it.
With criminal groups now reaping multimillion-dollar profits[22], ransomware attacks are likely to target larger organisations where the rewards are richer, perhaps focusing on holders of valuable intellectual property such as the health-care and medical research sectors. The Internet of Things (IoT) will likely be a target for cyber-criminals[23], with global networks of connected devices held to ransom.
While big organisations are likely to have appropriate technical safeguards, user education is still key - a lapse of judgement from a single person can still bring an organisation to its knees. For smaller companies, seeking (and following) cyber advice is crucial.
Given the huge scale on which cyber-criminals are now operating, we have to hope law enforcement and software security engineers can stay one step ahead.
Read more: Holding the world to ransom: the top 5 most dangerous criminal organisations online right now[24]
References
- ^ issued a fresh warning (www.abc.net.au)
- ^ study by security company Coveware (www.coveware.com)
- ^ AIDS Trojan (www.sdxcentral.com)
- ^ inelegant and easily undone (www.virusbulletin.com)
- ^ GameOver Zeus botnet (www.knowbe4.com)
- ^ Operation Tovar (www.fireeye.com)
- ^ 250,000 victims and potentially garnered 42,000 Bitcoin (www.zdnet.com)
- ^ Ransomware as a Service (www.upguard.com)
- ^ UK National Health Service (www.cbsnews.com)
- ^ estimated at up to US$4 billion (www.kaspersky.com.au)
- ^ Ryuk (www.crowdstrike.com)
- ^ Colonial Pipeline (www.abc.net.au)
- ^ JBS Foods (www.bbc.com)
- ^ Channel Nine network (www.cybersecurity-insiders.com)
- ^ reported occurrences of non-encrypted ransoms have doubled (secure2.sophos.com)
- ^ estimated US$20 billion in 2020 (pentestmag.com)
- ^ Ransomware as a Service (www.upguard.com)
- ^ cut of the ransom (www.zdnet.com)
- ^ Holding the news to ransom? What we know so far about the Channel 9 cyber attack (theconversation.com)
- ^ ten times more money (statescoop.com)
- ^ estimate (secure2.sophos.com)
- ^ multimillion-dollar profits (www.zdnet.com)
- ^ target for cyber-criminals (techcrunch.com)
- ^ Holding the world to ransom: the top 5 most dangerous criminal organisations online right now (theconversation.com)

















